And of course if I manually configure the client to trust my cert, the radius server's certificate can be properly validated and then 802.1x works. My goal is to be able to assign a machine to OU where this GPO will be applied and all the resulting 802.1.x and CA settings will be made without me having to touch the client machine at all. 4 SSIDs 1 Secondary Academy – Domain WiFi Setup. As all the settings required to connect can be pushed down via Group Policy Object. In part 1, we started to walk through deploying a 801.x wireless network. In this article, we will look at configuring the Network Policy Server (NPS) role, the access points, and finally pushing out the settings to clients via Group Policy. I boot up the laptop on a non-802.1x port to pull down all my 802.1X Group Policy settings, and just to be on the safe side I execute gpupdate /force. Then I reboot the machine on an 802.1X port, but none of the crucial NAP/802.1X services start. Group Policy Created Profile. Skip to the Export steps below. Manually Creating A Profile. Start this process on a clean machine that doesn’t have IEEE 802.1x Policies applied, otherwise you will have trouble. You can configure 802.1x Authentication on your LAN adapter in Windows by going to the Network Connections pane in the Control Panel.
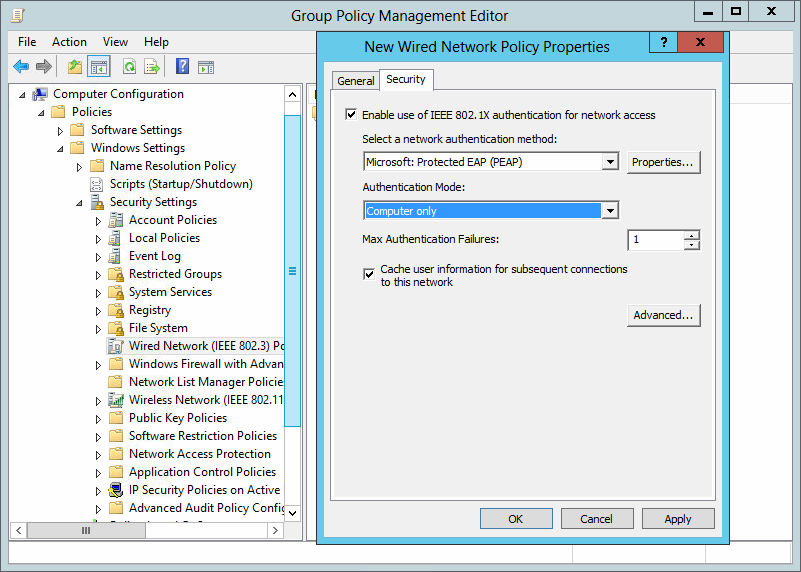
I have read some posts saying you can't have user and computer authentication and some that say you can, so I am a bit confused and not sure if I should implement both. I think I am also still working on determining how to setup user certs vs computer certs. We have a few older devices here and I was also wondering about the compatibility of them with EAP-TLS which I understand to be more secure than PEAP. This is my first time implementing something like this, so I am still researching it.


802.1 X Gpo Link

You can't have User and Device. It is either or. To validate via NPS you need to meet all conditions to get a RADIUS accept response. PEAP-MSCHAPv2 is fine as long as your clients trust the Server certs and users head the warnings when an invalid cert is used. However, if you are deploying your radius settings via GPO they should never see the warning. PEAP-TLS you have to deal with issuing client certificates.
I would like the user to have to fill in their credentials to a network and for the network to disconnect if the user's credentials change which will then prompt them to update their password to the new one, but am struggling to get this setup in GPO. I am certain that I am missing something. I am not sure if I am understanding correctly, but is it more secure to have the network setup that way? Or is it better to setup 802.1x in a different way? What does everyone else have setup? Poly universe free download game.

802.1x Gpo
Why? Wouldn't you want a seamless user experience, one where the device just works? Are these company devices?
